Sadržaj
File Carving with the Foremost tool
Abstract
File carving is an important subject area in computer forensics. It can be used by a forensics expert to recover hidden or deleted files and verify that those files were present on a suspected computer.
The purpose of this article is to explain what file carving is, what it is used for and how it is processed.
We will focus on the Foremost tool, what can be done with this tool and how to use it.
Keywords: file ; carving ; foremost ;
Introduction - What is file carving
File carving is a field of computer forensics in which we are searching for hidden or deleted files based on raw data from a disk or flash memory.
File systems all have metadata describing the hierarchy of stored documents (folders tree structure, files…) but file carving does not rely on these metadata but rather on raw data to identify and recover files.
A file can be identified by its header and footer for example a jpeg files raw data alays starts with 0xFFD8 and always ends with 0xFFD9.
We call these headers “magic numbers” or “file signatures”. A list of known file signatures can be found here: https://en.wikipedia.org/wiki/List_of_file_signatures .
The Foremost tool
What is Foremost ?
Foremost is a software designed for data recovering that is running on Linux machine in command line (there's no graphical user interface).
It was originally designed by Kris Kendall and Jesse Kornblum (special agents of the U.S. Air Force Office of Special Investigations ) in March 2001 and was updated by Nick Mikusas part of a master's thesis.
How does it works ?
The tool read and copy parts of the drive into the memory of the computer running the programm. Foremost then process file carving to search in the memory for a file header. When a file header is found the tool writes it in an output file and also writes the data following this header until a footer is found or until the possible size limit of the file is achieved. All the output files are written in an output directory allowing users to consult them.
A nice fact about foremost is that it is desinged for ignoring the file system so he can process file carving whatever the file system used on the investigated disk.
Where to find it ?
You can find the tool by following this link : http://foremost.sourceforge.net/ .
You can also get it by typing : “apt-get install foremost”in a terminal.
If you have Kali Linux , this tool is already installed and you can use it via command lines in the terminal.
How to use the tool ?
To use foremost you have to follow this syntax :
foremost [-h] [-v] [-d] [-vqWQT] [-b <blocksize>] [-o <dir>] [-t <type>] [-s <num>] [-i]
Here is the list of the possible options (you can obtain it by typing “man foremost ” in a terminal) :
- -h : Displays a help screen and exit
- -V : Show copyrhight information and exit
- -d : Turn on indirect block detection, this works well for Unix file systems
- -T : Time stamp the output directory so you don't have to delete the output dir when running ultiple times.
- -v : Enables verbose mode. This causes more information regardig the current state of the program to be displayed on the screen, and is highly recommended
- -q : Enables quick mode. In quick mode, only the start of each sector is searched for matching headers.
- -Q : Enables Quiet mode. most error messages will be suppressed.
- -w : Enables write audit only mode. No files will be extracted.
- -a : Enables rite all headers, perform no error detection in terms of corrupted files.
- -b number : Allows you to specify the block size used in foremost. This is relevant for file naming and quick searches. The default is 512.
- -k number : Allows you to specify the chunk size used in foremost.
- -i file : The file is used as the input file. If no input file is specified or the input file cannot be read then stdin is used.
- -o directory : Recovered files are written to the directory directory .
- -c file : Sets the configuration file to use if none is specified, the file “foremost.conf” from the current directory is used, if that doesn't exist then “/etc/foremost.conf” is used.
- -s number : Skips number blocks in the input file before beginning the search for headers.
Here is the list of the filetypes that foremost can recover :
jpg, gif, png, bmp, avi, exe, mpg, wav, riff, wmv, mov, pdf, ole, doc, zip, rar, htm, and cpp.
Using Foremost to recover files from a disk image
In this example I will use the Foremost tool in order to recovers images from a phone raw image.
The image I used for this example (deviceImage.raw) is taken from the second laboratory of my computer forenics course. It is an image of a phone that belongs to a supposed hooligan.
The first thing to do is to create an ouput directory.
I chose to create it in the Desktop directory : mkdir /root/Desktop/output
We can now start to use foremost to recover files from our disk image.
Open a terminal and type : foremost -i path_to_your_image -o path_to_your_output_directory
ie.
foremost -i /root/Desktop/deviceImage.raw -o /root/Desktop/output
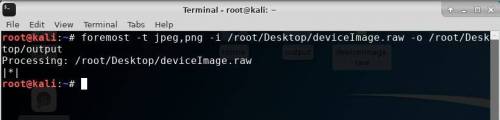
Foremost will then process to recovers all the files he found on the image.
When foremost has finished processing you can open the output directory.
You will find an audit.txt file and several folders , one for each file type of the files recovered by foremost.
The audit file contains :
- The start date and time of the recovering
- The command in which foremost was invoked
- The configuration file used
- The image used
- The list of the recovered files
- The number of files recevored per file types
- The end date and time of the recovering
Then if you navigate in the directories you will be able to find the files recovered by foremost.
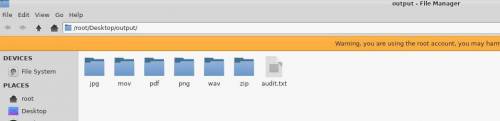
ie. You will find all the jpg files recovered in the image in the directory …/output/jpg/ .
If you already know what file types you are searching you can specify it to be quicker :
ie. We only want to recover the jpg and png files :
foremost -t jpg,png -i path_to_your_image -o path_to_your_output_directory
Warning :
You will probably encounters an error when running foremost a second time.
To avoid it there's two solutions :
- Empty the output directory before running foremost a second time
- Use the -T option, it will create an output directory with the timestamp in the directory name.
Using foremost to recover file hidden in an image
It is possible to use the foremost tool to recover files hidden in an image.
To hide a file in an image is quiet easy, let's see how to do it.
On Windows :
You can use this command in the cmd to hide a file inside an image :
copy /b name_of_initial_img + name_of_file_to_hide resulting_image_name
On Linux :
Create a directory , store in this directory all the files you want to hide.
Put the image and the directory in a folder.
Creates an archive from the directory to hide.
Then use this command to hide the archive in the image :
cat image.jpg secret.zip > image_and_hidden_files.jpg
To recover the files hidden we can use the foremost tool, we just have to specify that the suspected image is the input file :
foremost -i image_and_hidden_files.jpg -o …/output
The hidden files will appears in the output directory.
Conclusion
Foremost is a powerfull tool for file carving since it ignore the file systems and only looks at the raw data.
It israther quick and simple to use.
It can easily be used to recover files from a disk image.
